Online security is becoming more and more critical to the everyday life of anyone using the internet on a regular basis. Whether you’re interested in maintaining a secure and private connection for personal safety, in keeping your boss from tracking your internet use or keeping Big Brother in check, using a VPN as part of your multiple levels of online security is a good idea.
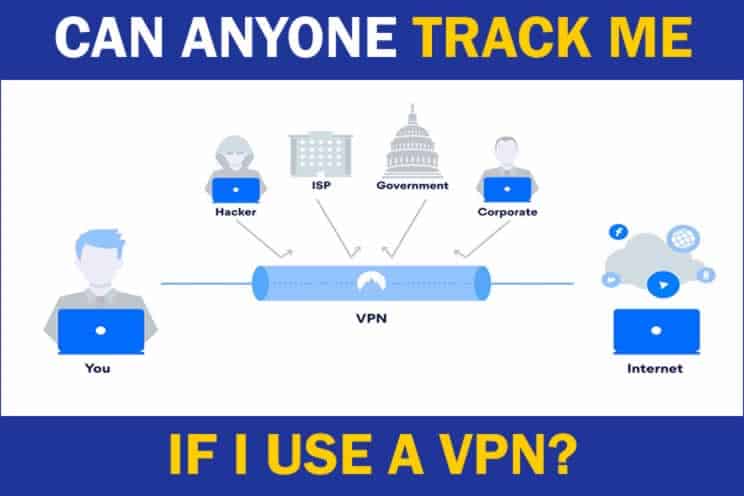
Can anyone track me if I use a VPN? A reputable VPN will make it difficult to track someone as they will have better security at protecting their customers real IP address from being divulged. Without knowing the real IP address being used, it makes it difficult to work out a persons identity unless the VPN gives this away.
To further understand how tracking can done, it’s important to understand what a VPN actually does and how it can help remain anonymous.
What is a VPN?
According to the National Counterintelligence and Security Center, Iranian computer hackers stole $3.4B – yes, that’s 3.4 Billion Dollars – worth of DATA from US Universities in one month during 2018. Just. One. Month. Alone.
Virtual Private Networks (VPNs) have been a necessity since groups started working online. Protecting intellectual property discussed in bulletin boards was essential. It wasn’t until 1996 that a Microsoft employee developed the first point-to-point tunneling protocol (PPTP). At that point, the beauty of the VPN’s evolution began.
The best way to describe the difference between a PPTP and a VPN is that virtual private networks begin at the source – your computer. Its intent is to provide an encrypted, secure portal between your computer and other computers or servers. An internet within the internet, as it were.
An effective VPN service masks your actual identity and location before the local ISP (internet service provider) receives your request for connection.
Say you’re sitting in the local coffee shop with its non-secure, open network. Anyone with any level of hacking skills can get on that network, see who’s on the network, and the sites they’re accessing.
This means that any data you’re exchanging with that site you’re visiting is also available to that nefarious individual sitting outside in the car, eavesdropping on your online conversation. Having a good VPN service helps you block that thief. Think of it like a forcefield around you and your data that allows you to see out, but others can’t peer inside (check out my list of reputable VPNs here).
What is a Good VPN Service – What are the Differences?
We’ve already identified the PPTP as one of the first privacy protocols developed that was available to the general public. None of us are ignorant enough to believe governments didn’t have privacy protocols in place before they were available to the average Jack and Jill.
The thing is that although it is still offered as a privacy and security measure, by today’s standards, it really isn’t secure – the coding is too basic and easily cracked.
Four Other Available Protocols
That said, PPTP used in conjunction with additional security protocols can be very effective. Here are examples of the other security protocols:
1. L2TP/IPsec – Layer 2 Tunneling Protocol/Internet Provider Security
This is what it says – the next generation of the tunneling privacy protocol. This one was developed by Cisco and is an improvement over the PPTP. It uses a specific generated key to open both ends of your internet connection between your device and your targeted location.
There are unverified rumors that this is a security protocol that can be hacked by the NSA (National Security Agency). This would mean they can see what’s being transmitted to and from your device. Whether or not that’s accurate, there’s enough concern in the online community to raise it as a potential privacy issue.
2. SSTP (Secure Socket Tunneling Protocol)
Not to be outdone, Microsoft developed this next level protocol.
This process allows for the transmission and encryption of data while checking for the integrity of the traffic on the connection. It’s available for use in most Windows environments that are on the Vista release or more recent.
One downfall of this security protocol is that it requires more bandwidth than the others. That makes sense because it is, in effect, hiding your data within additional data. This may occasionally result in sites that aren’t built for enhanced security timing out, and thereby frustrating you and the end-user.
Here’s the thing, though. If the site isn’t built to be secure enough for this bandwidth level of security, do you really want to give them your private information? This is generally a security solution you can count on.
3. IKEv2 (Internet Key Exchange, version 2)
Not one to rest on their proverbial laurels, Microsoft improved on the SST protocol with this level of security. It’s among the best level of security available on the open market.
During this process, both ends of the tunneled connection are independently encrypted, making it nearly impossible for anyone to obtain data from either side of the data exchange.
4. Open VPN
This is an open community build that is in a constant state of process improvement. It takes what’s best from each of the security protocols discussed above and enhances those features.
Can you imagine taking those brilliant minds that like to be known for being the best coders and having them working for your security? That’s what this is—the best of the best.
How to Incorporate a VPN into Your Security Protocols
You probably noticed a consistent theme in the protocol developments just discussed… Microsoft. Hey. They’re not an international conglomerate for nothing.
That said, while this absolutely is not an ad for them, the fact is that if you have Microsoft Windows-based software on your devices, you’re going to have an easier time using some of these solutions than an iOS or Android system might.
Even so, there are some general guidelines you’re going to want to consider when exploring what VPN protocol to add to your monthly security subscription.
You Get What You Pay For… Kind of
There are free VPN products and apps available, but the reality is those apps need to make money somehow. If they’re not making money directly from you, how are they funded? Is it possible they are selling your information to their third-party advertisers? It’s something to consider.
On the opposite end of the scale are the VPNs that are big business and will charge you a discounted price of more than $10 per month. Considering some of the excellent solutions on the market, this is a lot to pay.
The most often recommended solutions are:
- NordVPN – at an undiscounted price, they’re over that $10 per month mark, but they also offer deep discounts for longer relationship commitments.
- Surfshark – this company will also offer deep discounts on their monthly subscription fee for your willingness to commit to a multi-year guarantee.
- ExpressVPN – they offer the least amount of discount, but still make their services affordable.
But… Can I Be Tracked Using a VPN?
Yes. There aren’t any companies that are exempt from subpoenas. If your VPN company is served with legal action, they are required to provide the logs they have regarding your activity.
Before you subscribe to any security service, make sure you read that small print in their user privacy section – especially understand the How We Use Your Data piece.
With that in mind, unless you’re planning on being one of those bad actors with ill intent, secure VPNs are in your best interest to protect your activity from being tracked.

