
The Tor network provides a way of remaining anonymous on the internet and many people assume they don’t need a VPN because of this. I decided to take a deeper look into using Tor without a VPN to find out if this still provided the levels of protection a VPN can provide.
What happens if you use Tor without a VPN? Using Tor without a VPN could allow the operators of the Tor exit nodes to see your information or tamper with it, as it travels through their exit nodes. By using HTTPS downgrade attacks, encrypted HTTPS connections could still be snooped upon by forcing the connection to use HTTP as it leaves the Tor exit node.
Whilst Tor can help in maintaining your privacy and keeping you anonymous on the Internet, it doesn’t offer the level of protection a VPN offers. As the connection leaving the VPN server can end up being better protected than a connection leaving the Tor network’s exit node.
This is because with a reputable VPN, the VPN server is under the control of the VPN provider whilst the Tor exit node is operated anonymously. The Tor exit node could be run by people who are intent on keeping with the goals of the Tor project or they could be malicious parties, like hackers, government agencies or even rogue states.
Let’s take a look at how Tor works without using a VPN to see potential issues in privacy and protection.
Using Tor without a VPN
The way in which the Tor network works is by channeling connections made from the Tor software installed on your device through a network of global Tor nodes. With special Tor nodes known as exit nodes providing an exit point from where the connection leaves the Tor network and carries on along the normal Internet routes to the website being connected to.
The website will only see the IP address of the Tor exit node, making it difficult to trace who made the connection and it’s this difficulty in tracing connections, that gives Tor the ability to provide privacy protection and keeps its users anonymous. On top of this the Tor nodes keep changing in number with new nodes being added and existing nodes being removed, crucially making it even more difficult to trace the connections being made.
There are a number of issues with the Tor network where privacy could be compromised, with the main one being the Tor exit nodes. These exit nodes potentially allow anyone who is running the exit node to access the information passing through the exit node.
Encrypted information passing through over HTTPS, SSH and SFTP connections, is difficult to access but there are still many connections made using the more insecure HTTP and FTP connections. These connections don’t use encryption and travel through the Tor network in plain text, allowing the owner of the Tor exit node to be able to read the information.
When the domain for a website is entered without the HTTPS part, for example vpnsuccess.com, the connection is first made using HTTP. This initial connection is not encrypted but fortunately, an automatic redirect occurs when the HTTP connection is made to where vpnsuccess.com is hosted and this redirects to the securer HTTPS for any subsequent connections made.
Someone running a Tor exit node could intercept the initial HTTP connection and stop them from being redirected to HTTPS, making all the communication take place using the unencrypted HTTPS channel. This would allow any information sent across the connection to be seen by the malicious owner of the Tor exit node, thereby compromising security.
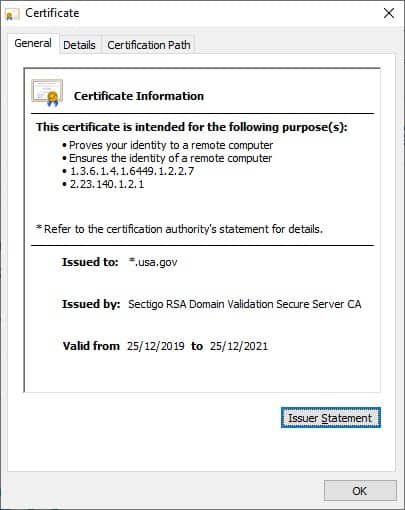
It’s important to always make sure the padlock is showing on the left hand side of the address bar when making any connection to a website using a secure connection. As otherwise, all information entered into the web page will easily be captured by operator of the Tor exit node. I always check the certificate of the connection by clicking the padlock icon and seeing if the details look correct (example of US government certificate shown below).
Using Tor with a VPN
The type of attack mentioned in the previous paragraph is known as a HTTPS downgrade attack and by using a VPN, this type of attack becomes extremely difficult to mount. As the VPN provides end-to-end encryption from the users device (VPN client software) to the VPN server. This secure tunnel is maintained across the Tor network and when this connection traverses across the Tor exit nodes, it is difficult to break the connection.
The VPN connection doesn’t use HTTPS, instead it uses special VPN protocols like OpenVPN, WireGuard to L2TP/IPSec. Some VPN protocols like PPTP aren’t as secure and should not really be used.
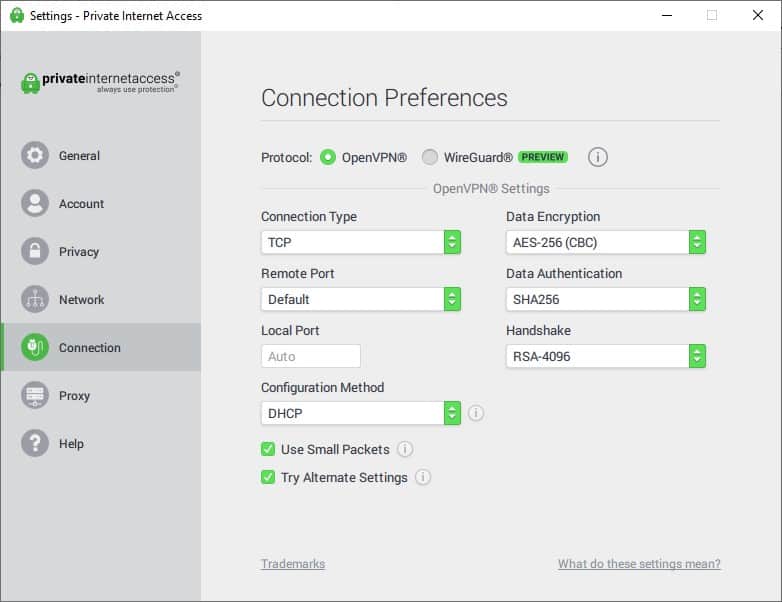
In the screenshot above, the OpenVPN protocol is used and this has been around since 2001. The level of encryption is customizable, making it possible to use military grade levels of encryption that are near impossible to break.
There are two different ways of using Tor together with a VPN:
- Tor over a VPN connection
- VPN over a Tor connection
Tor over a VPN connection
By first connecting to the VPN server and then opening the Tor browser allows the Tor connection to take place over the VPN. This allows the fact that Tor is being used from your Internet Service Provider (ISP) as they will not be able to see the connection to the Tor network, as they will only see a connection to the VPN server.
The other advantage of connecting to Tor over a VPN is the Tor network will only see the IP address assigned by the VPN and not the real ISP assigned IP address.
The disadvantage of connecting to Tor over a VPN is any malicious Tor exit nodes could still use HTTPS downgrade attacks to try to access or tamper with the information exiting their nodes.
VPN over a Tor connection
By first opening the Tor browser, without entering anything into it, followed by connecting to a VPN server, an encrypted VPN channel will be created, providing better protection against malicious Tor exit node snooping.
Anything typed into the Tor browser will start passing through the Tor network and once it reaches the exit node, the encrypted data travels to the VPN server, before exiting the VPN server and carrying on its journey across the internet. The Tor exit nodes will find it difficult to hack into the encrypted connection and this will protect the data passing through confidentiality and integrity.
The IP address will be the IP address assigned from the Tor network, making it difficult for the VPN to see real IP address but this won’t really matter too much, as the VPN provider will already know your identity if you’ve purchased a subscription with them.
This approach of using VPN over a Tor connection provides a double layer of protection with Tor providing anonymity and the VPN providing the security of encrypted connections.
Is Tor and a VPN enough?
Using Tor with a VPN and preferably with the VPN over the Tor connection should be enough to protect privacy. The biggest risk with Tor are the exit nodes as some of these can be under the control of malicious parties like rogue states, hackers and the like.
By using a VPN over Tor setup, all traffic leaving the exit node will be encrypted to a high level making it extremely difficult for any operator of an exit node to break into this traffic and see the information contained within.

